Information Security Software
Protect your information assets, manage risks. ISO 27001 compliant information security management system.

Cyber threats are increasing every day, and data breaches lead to significant costs. A systematic approach is essential to protect your information assets. TOKU Information Security Software , with its ISO 27001 compliant structure, enables you to manage all your ISMS processes, from asset inventory and risk analysis to control management and incident response, on a single platform.
Current Challenges
- The asset inventory is not up-to-date.
- Risk analysis is performed in Excel.
- SOA tracking manually
- Security incidents are not being recorded.
- Compliance with the Personal Data Protection Law is difficult to achieve.
TOKU Solution
- Dynamic asset inventory
- Automatic risk scoring
- 114 checkpoint SOA tracking
- Incident management and response
- Integrated GDPR module
Reliable Information Security
Asset Inventory
Classify all your information assets, assign owners to them, and define their relationships.
Risk Matrix
Assess threats and vulnerabilities, score risks, and record action decisions.
SOA Management
Determine the applicability of Annex A controls and monitor their implementation status.
GDPR Integration
Personal data inventory, VERBİS notification and information text management.
System Images
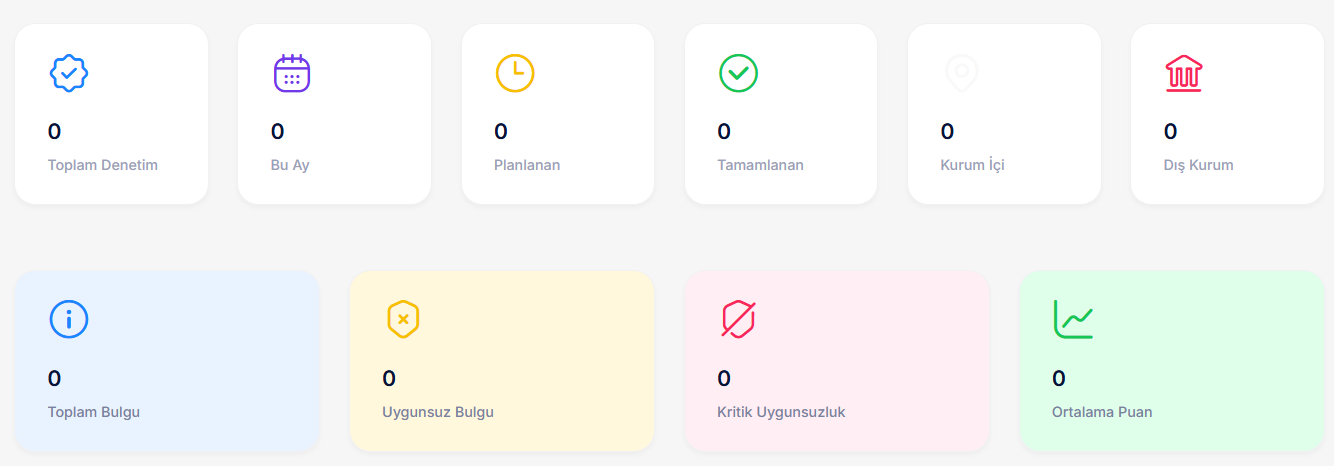
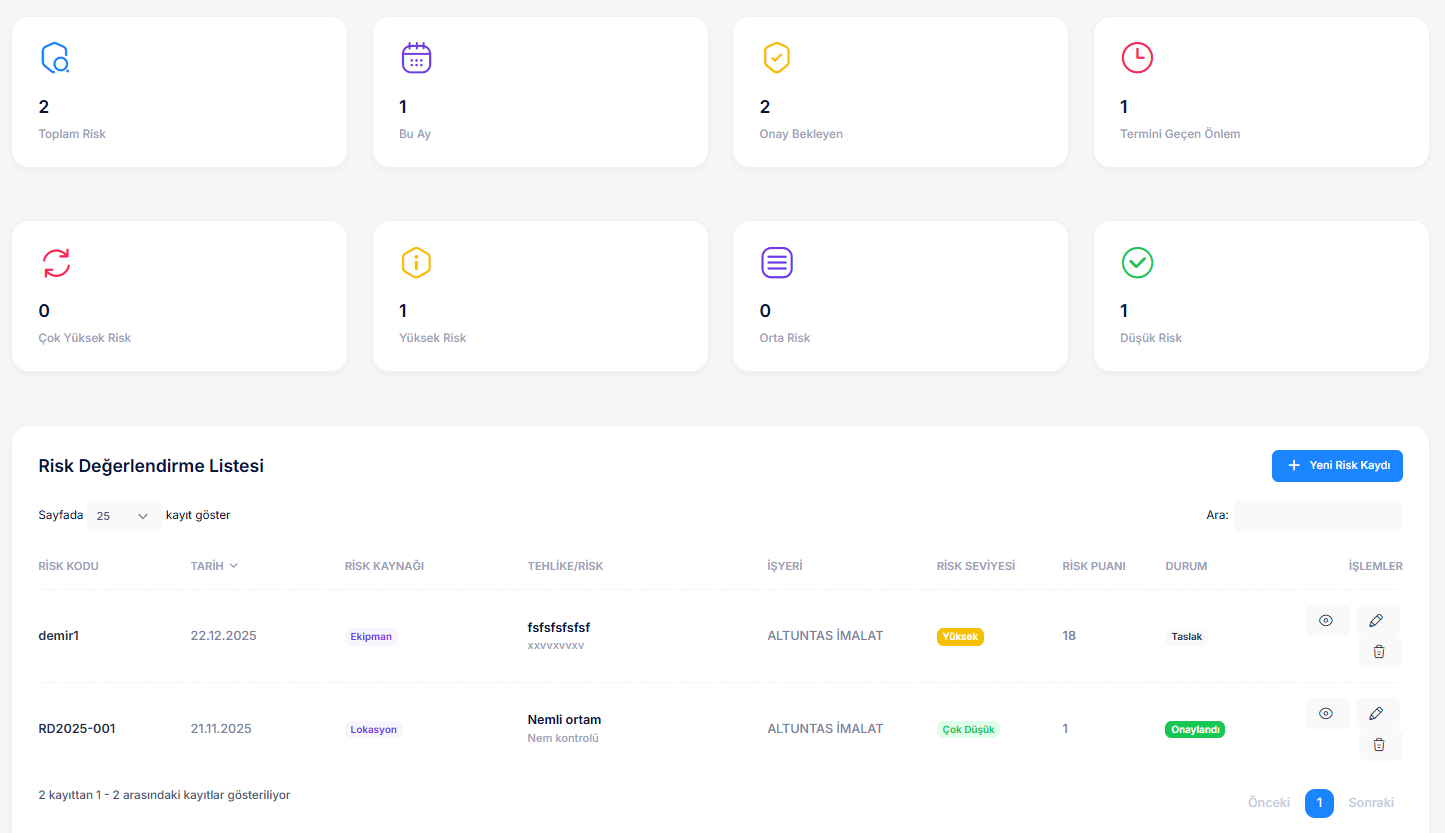

Tangible Outcomes
Results you will achieve with an information security system
ISO 27001 Certificate
ISMS documentation ready for international information security certification.
Risk Reduction
Significant reduction in the risk of cyberattacks, data breaches, and business interruption.
GDPR Compliance
Full compliance with personal data protection legislation and VERBİS notification.
Information Security Modules
Asset Management
Inventory and classification of information assets.
Risk Assessment
Threat and vulnerability analysis, risk scoring.
Control Management
Annex A checks and implementation monitoring.
Incident Management
Security incident recording and response.
Policy Management
Security policies and procedures.
Access Management
User permissions and access control.
Key Features
Asset Map
Information assets and relationships
Risk Matrix
Visual risk assessment
SOA Tracking
Statement of Applicability
Reporting
Management and audit reports
Protect your data.
Request a demo for professional information security management.